‘Simplicity is the ultimate sophistication’ for Access Control

By Tim Boivin (pictured), Marketing Director, PortSys Leonardo DaVinci’s philosophy in the headline has never rung so true as it does today in IT – especially when we’re talking about providing users secure access in our perimeterless world. If your access approach is wrong, your risk of being hacked ramps up exponentially. Counterintuitively, installing more security […]
What an Endpoint is, and how EDR can benefit business

By Eleanor Barlow, Content Manager, SecurityHQ An endpoint, in its simplest form, is any device that can be connected to a given network, including, and not limited to laptops, computers, mobiles, servers, IoT devices, switches, cameras, digital printers, smart watches, and more. What constitutes as an endpoint is growing by the day. Be it in […]
How hackers get caught

Cyber criminals are intelligent, elusive individuals, making it difficult for law enforcement to track them down. Not all hackers manage to escape retribution, however. Here, Joanne Newton, deputy head of the school of computing at Arden University, explores the traps they fall in to, and how they get caught… Cyber criminals go to many lengths […]
Five top tips for improving your cyber security visibility and control

By Leyton Jefferies, Head of Security Services, CSI With an increasing number of high-profile security breaches splashed across the media, companies are now looking to improve their cyber security. As the world has become more digitally connected and working from home continues to be part of the way we work, there has become more opportunity […]
Salesforce security: 5 ways your data could be exposed

By Varonis Salesforce is the lifeblood of many organizations. One of its most valuable assets-the data inside-is also its most vulnerable. With countless permission and configuration possibilities, it’s easy to leave valuable data exposed. That, coupled with the fact that most security organizations aren’t very familiar or involved with Salesforce’s administration, opens organizations up to massive risk. Here […]
WEBINAR REWIND: The next generation of secure digital communications – Why now and why it matters
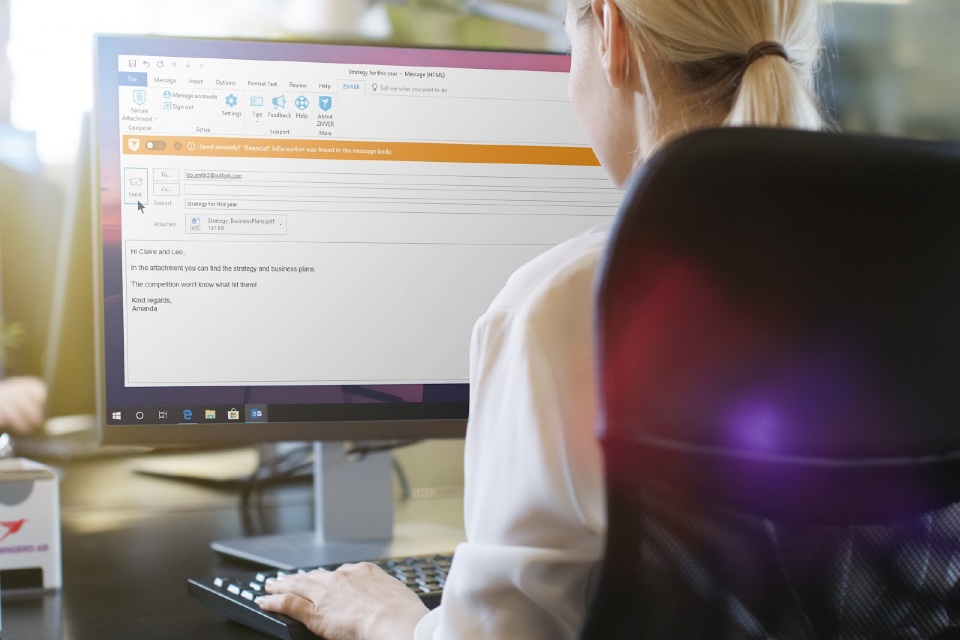
Don’t worry if you missed December’s fantastic Zivver webinar ‘The next generation of secure digital communications – Why now and why it matters‘ – You can now watch the entire session again online! Regulatory reforms, digital transformation, hybrid working… The business landscape continues to evolve and the need for secure and compliant digital communications solutions […]
Cybersecurity in 2022: A view from the experts

There is no doubt that this year has been a year of disruption, change and opportunity within the cybersecurity industry. With 2022 on the horizon, find out what the experts have to say about the top trends impacting the industry now and what to look out for in the future… Carlos Morales, VP Solutions, Neustar Security […]
Forrester Consulting research shows Human Layer Security is the solution security leaders have been looking for

A commissioned study conducted by Forrester Consulting on behalf of Tessian shows that Security and Risk leaders feel little control over risks posed by employees. On the other hand, organisations that deploy Human Layer Security technology feel more prepared to face email security threats and data breaches, demonstrating a higher level of security maturity. Key insights […]
Cloud applications put your data at risk — Here’s how to regain control

By Yaki Faitelson, Co-Founder and CEO of Varonis Cloud applications boost productivity and ease collaboration. But when it comes to keeping your organisation safe from cyberattacks, they’re also a big, growing risk. Your data is in more places than ever before. It lives in sanctioned data stores on premises and in the cloud, in online collaboration […]
International Fraud Awareness Week – Hear from the experts

Fraud is not a new concept – far from it. Since the dawn of time, fraudsters have looked to take advantage of circumstance and innocent people have fallen victim as a result. But, in our digital age, fraud is more prevalent than ever before. That’s why this International Fraud Awareness Week, we spoke to three […]


