McAfee unveils new enterprise security portfolio
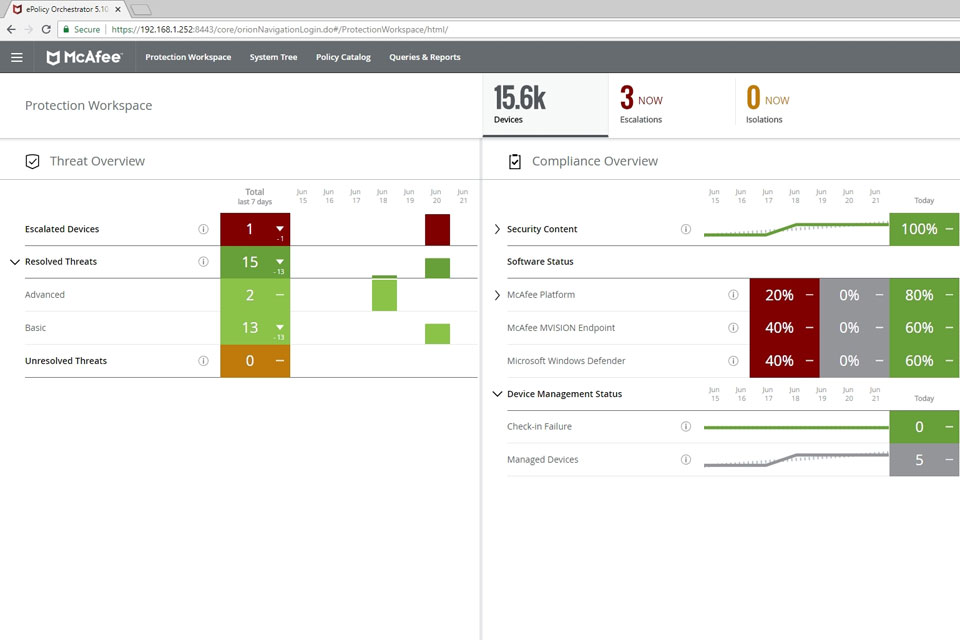
McAfee says its new MVISION portfolio offers a comprehensive, flexible defense system that manages security products with multiple devices and the cloud in mind. Specifically, the firm says MVISION strengthens the device as a control point in security architectures by delivering simplified management, stronger Windows security, behavior analytics, and threat defense for Android and iOS […]
Risk-based approach needed to stop cyber crime

A report by Gartner has advised companies to take a risk-based approach to stop cyber crime, rather than trying to prevent attacks with large-scale, expensive security deployments. A survey commissioned by Gartner of 3,160 CIOs across 98 countries and various major industries showed that 35% had already invested in a form of digital security at […]
Microsoft launches identity bug program

Microsoft has unveiled a new bug program that rewards researchers for discovering vulnerabilities in Microsoft’s Identity services up to $100,000. Rewards offered range from $500 to $100,000 for any flaws found that impact a range of services, including Microsoft and Azure Active Directory accounts, OpenID and OAuth 2.0 standards, Microsoft Authenticator applications for iOS and […]
UK firms ‘overconfident’ on cybersecurity
Business are displaying a false sense of security when it comes to their IT security, flying in the face of evidence showing rising incidents of cyber attacks. That’s the conclusion of a study conducted by Ovum on behalf of US-based analytics firm FICO, which found that three quarters of UK execs felt their firm was […]
Security IT Summit 2019: Save The Date!

The next Security IT Summit will take place on July 2nd 2019 at the Hilton London Canary Wharf – secure your place today! The event will provide you with a rare full working day of networking, learning and connection building – plus cost-saving cybersecurity solutions. In short, the Security IT Summit will enable you to […]
Do you specialise in Authentication Systems? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – in August we’re focussing on Authentication Systems. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Authentication specialist and would like […]
UK government introduces ‘Minimum Cybersecurity Standard’

The UK government has outlined the minimum cybersecurity standards that it expects for its own day-to-day operations in a new document developed in collaboration with the National Cyber Security Centre. Over time, the measures will be incremented to continually ‘raise the bar’, address new threats or classes of vulnerabilities and to incorporate the use of new […]
Nine graduates pass through NCSC Cyber Accelerator
A group of tech start-ups have become the latest to graduate from a Government initiative to advance the next generation of cyber security systems. The nine-month GCHQ Cyber Accelerator (now renamed the NCSC Cyber Accelerator), delivered in partnership with Wayra UK, part of Telefónica Open Future, saw nine companies develop cutting-edge products and services to […]
NHS inks three-year cybersecurity partnership with IBM

NHS Digital has entered into a three-year strategic partnership with IBM to provide a range of new and improved services to health and care organisations. The additional services will expand NHS Digital’s existing Cyber Security Operations Centre (CSOC)3 and enhance NHS Digital’s current capability to monitor, detect and respond to a variety of security risks […]
EVENT REVIEW: Security IT Summit

The cybersecurity industry event of the year took place earlier this week, with Telefonica o2 and more sharing their expertise with delegates. The event, which took place at the Hilton London Canary Wharf, brought cybersecurity professionals together for one-to-one business meetings, interactive seminars and valuable networking opportunities. Over a full working day, delegates met with solution […]
