Weak authentication will be subject of increasing exploitations by AI Agents, says research
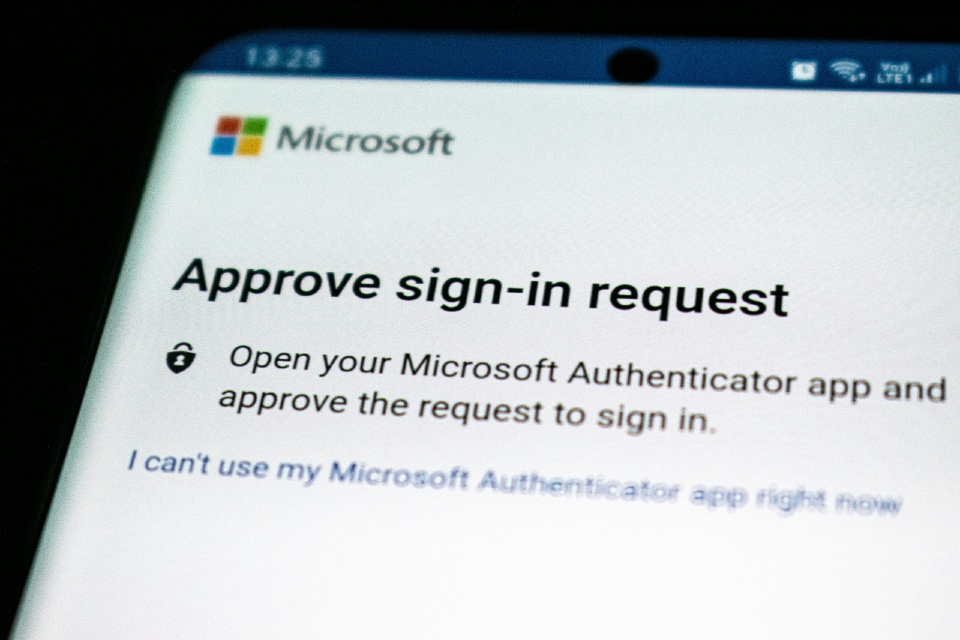
AI agents will reduce the time it takes to exploit account exposures by 50% by 2027, according to analysts at Gartner. “Account takeover (ATO) remains a persistent attack vector because weak authentication credentials, such as passwords, are gathered by a variety of means including data breaches, phishing, social engineering and malware,” said Jeremy D’Hoinne, VP Analyst […]
AUTHENTICATION MONTH: Securing your gateways by choosing the best solutions

Robust authentication is paramount for organisations across the UK’s public and private sectors. As a senior IT professional, selecting the right authentication solution is crucial for safeguarding sensitive data, maintaining business continuity, and protecting your organisation’s reputation. Here are some top tips to guide your search for a trusted authentication solution… Understand Your Organisation’s Needs Prioritise Security and Functionality […]
If you specialise in Penetration Testing solutions we want to hear from you!

Each month on Cyber Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in August we’re focussing on Penetration Testing solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a Penetration […]
AUTHENTICATION MONTH: The rise of sophisticated authentication in retail & banking fraud prevention
Fraudulent activity is a persistent threat for both retail and banking sectors in the UK. Senior IT and anti-fraud professionals are constantly on the lookout for robust authentication solutions and related services to fortify their defences against ever-evolving scams and safeguard customer funds. The landscape of authentication is experiencing a significant shift, with technology playing […]
If you specialise in Authentication solutions we want to hear from you!
Each month on Cyber Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in July we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a Authentication solutions […]
Gatekeeping Digital Realms: Top tips for effective Authentication in cybersecurity

The first line of defence in protecting digital assets and data is effective user authentication. Ensuring the right individuals have access to your systems is paramount to maintaining a robust cybersecurity posture. Here, we explore key tips for optimising your authentication processes… Adopt Multi-Factor Authentication (MFA): MFA adds an extra layer of security to your […]
Do you specialise in Authentication? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in July we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Authentication solutions […]
Do you specialise in Authentication? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in July we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Authentication solutions specialist and would […]
Do you specialise in Authentication Security? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in July we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a Authentication solutions specialist and […]
Do you specialise in Authentication solutions? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in July we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Authentication solutions specialist and […]


