ACCESS CONTROL MONTH: Combatting insider threats and data breaches

Insider threats remain one of the most significant cybersecurity risks for organisations. Whether caused by malicious intent, negligence, or compromised credentials, insider threats account for a growing number of data breaches. With sensitive data and critical systems at risk, businesses must adopt advanced access control solutions to mitigate insider threats and enhance cybersecurity resilience. By leveraging role-based access control (RBAC), […]
ACCESS CONTROL MONTH: The ‘never trust, always verify approach’ to security

With cyber threats growing more sophisticated, organisations in the private & public sectors are embracing the Zero Trust security model to enhance access control and reduce attack surfaces. Traditional perimeter-based security approaches are no longer sufficient, as remote work, cloud computing, and hybrid infrastructures increase exposure to cyber risks. Zero Trust access control ensures that no user […]
ACCESS CONTROL MONTH: Which solutions are right for your organisation?

Access control is a critical pillar of cybersecurity, protecting organisations from unauthorised entries, data breaches, and insider threats. As cyber threats become more sophisticated, businesses must adopt advanced access control solutions that provide scalability, compliance, and seamless integration with existing cybersecurity infrastructure. Choosing the right solution requires a strategic approach, evaluating cloud-based access control, biometric authentication, and multi-factor authentication […]
ACCESS CONTROL MONTH: Weighing up biometric vs. traditional authentication

Traditional authentication methods such as passwords and smart cards are being challenged by biometric authentication, including fingerprint scanning, facial recognition, and behavioural biometrics. But which approach offers the best combination of security, usability, and scalability? Here we examine the strengths and challenges of each… 1. Traditional Authentication: Still Relevant in 2025? Traditional authentication methods have long been the standard […]
February 2025 is Access Control Month on Cyber Security Briefing – Here’s how to get involved!

Each month on Cyber Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in February we’re focussing on Access Control solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Access […]
ACCESS CONTROL MONTH: Navigating the Maze – Sourcing trusted access control solutions for CIOs

Securing physical and digital access is paramount for any organisation. For Chief Information Officers (CIOs), the responsibility of selecting a trusted access control solutions provider carries significant weight. This article explores key approaches to guide CIOs in navigating the diverse landscape and finding the ideal partner… 1. Define Your Needs Clearly: Start by conducting a […]
ACCESS CONTROL MONTH: Establishing the key pillars of best practice

Implementing an effective access control regime is paramount for IT security professionals in the UK’s public and private sectors. Access control systems are essential for protecting sensitive information, ensuring that only authorised users can access specific data and systems. Here are the key pillars for establishing a robust access control regime, based from input from […]
Smart access: What if biometrics were the foolproof solution for infrastructure protection?
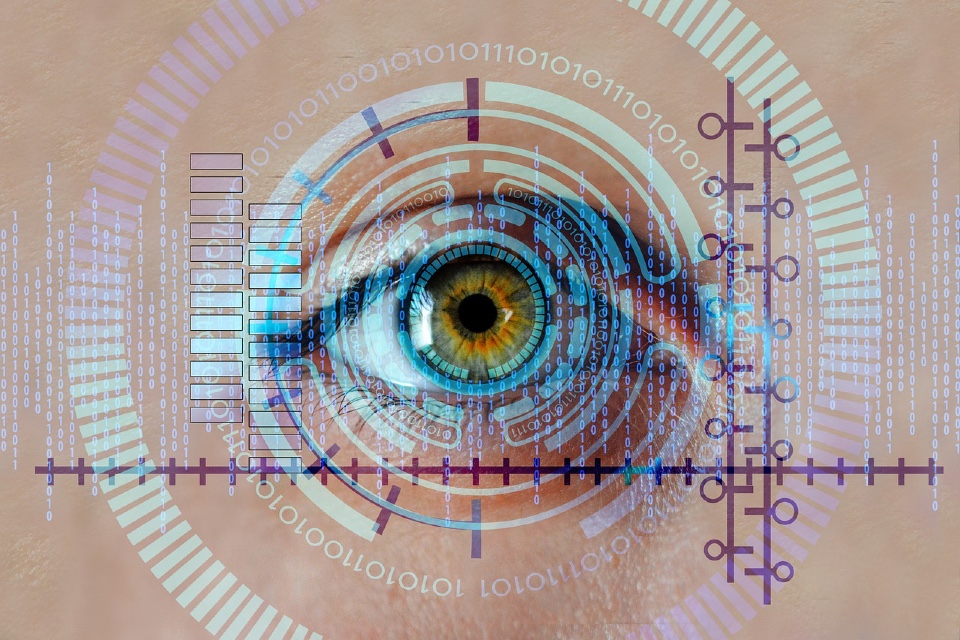
By Céline Littré, Product Marketing Manager at Linxens Biometrics are already well known and used in sectors such as identity and payments, but their use could also be relevant to access control for both IT and physical infrastructures? Access to IT infrastructures As the number of reported cyber-attacks has multiplied, companies, which until recently were […]
Do you specialise in Access Control? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in February we’re focussing on Access Control solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Access Control solutions […]
Growing demand for future-proof mobile solutions for access control

With convenience being a major theme, 42% of respondents worldwide indicate plans to upgrade to mobile-ready systems. That’s according to the latest State of Access Control report produced by IFSEC Global in partnership with HID Global, which surveyed just over 1,000 respondents from across North America (56%), EMEA (29%) and Asia Pacific (15%) to detail […]


