By Carolyn Reuss, director, product management at Secureworks & Pierre-David Oriol, senior consultant, product management at Secureworks
The explosion of data and devices is expanding the attack surface from the core to the edge. Cyber threats continue to rise, and cybercrime continues to accelerate. To achieve better security outcomes, security administrators need broad visibility across multiple sources and over time, to identify unknown threats.
The following outlines how Secureworks’ ManagedXDR coupled with Incident Response, detected malicious activity as Microsoft Exchange servers attempted to run a version of China Chopper web shell.
The most effective cyber defenses combine talent and technology. The two are not mutually exclusive. As the integrated response to this particular incident will demonstrate.
Early Monday, March 1, Secureworks Security Operations Center (SOC) analysts contacted the Secureworks Counter Threat Unit (CTU) researchers to report that Secureworks Taegis XDR (Extended Detection and Response) detected malicious activity via its endpoint telemetry across several customers as Microsoft Exchange servers attempted to run a version of China Chopper web shell.
Initial Response and Findings
The SOC’s note initiated a routine response, engaging CTU researchers, Incident Response (IR) Teams, and engineers to collect critical, relevant intelligence such as initial attack vector, attack failures and successes, impacted customers (by looking back over a year’s worth of event data), and importantly, understanding the intent. This demonstrates that while XDR’s detection capabilities stand on its own for an individual instance, ManagedXDR working in concert with other systems and human resources amplifies the “network effect” when observing an event that impacts multiple organisations, and the whole XDR community benefits.
In this event, endpoint telemetry was critical to detecting and understanding the threat. Looking across customers’ endpoint telemetry, the team identified related intrusion activity across the affected businesses.
The next day, once we had a comprehensive understanding of the threat, we released CTU TIPS to inform customers of the targeted campaign and provide initial recommendations. This was followed by automated XDR notifications about the threat at log-in. Additionally, Microsoft released out-of-band patches for on-premises Microsoft Exchange Servers that organisations with vulnerable systems needed to apply ASAP.
Dealing with Vulnerabilities
Vulnerability management is another vital element to this coordinated detection and response. Secureworks Taegis VDR (Vulnerability Detection and Response) helped affected businesses quickly identify and prioritise vulnerabilities in their environment. In this case, we automatically factored in specific vulnerabilities heightened by recent incidents and public interest into VDR, and delivered detections for CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 as details about this vulnerability continued to surface.
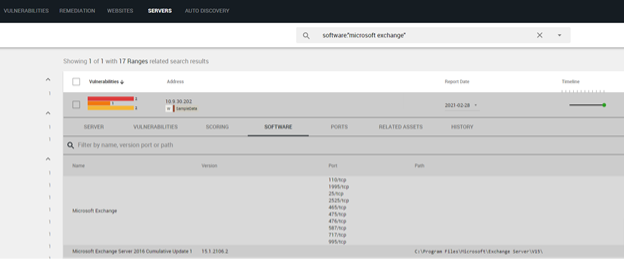
VDR provides businesses with the ability to search specifically for certain software (e.g., <software:“Microsoft Exchange”>) to accelerate their VM cycle outside of their regular scans and identify existing vulnerable assets. The contextual prioritisation engine allows businesses to easily identify which vulnerabilities create the highest risk in their environment. That risk is always subject to each organisation’s internal context, from which VDR continuously learns.
In this case, as the attack was exploiting unpatched on-premises Exchange Server versions 2013, 2016, and 2019, as such, VDR helped those organisations that were impacted to understand which of the occurrences of the above CVEs to address first, saving security experts critical triaging time. Businesses can either search specifically for Microsoft Exchange, (as shown above), or work from reliable detections for these CVEs, to confirm the finding is, or is not, a priority in comparison to other vulnerabilities within their environment.
Incident Response & Engagement Support
Working in tandem with their other colleagues, the IR team immediately started working with customers who had seen exploitation of their Microsoft Exchange servers from this activity, providing guidance on the remediation steps and identifying any further activity.
Additional Steps You Can Take
The threat is still live, so we recommend the following steps, if applicable, to keep your organisation safe:
- If you have on-premises versions of Exchange with the vulnerability, and you have concerns, invoke your incident response, whether it’s through our team, internally or through your Managed Security Services Provider (MSSP), to investigate whether access has been leveraged by the threat actor that Microsoft is currently referring to as HAFNIUM.
- Organisations using affected on-premises versions of Exchange Server should apply updates immediately, if possible. Please note that Exchange Online is not affected.
- Organisations should also closely monitor Exchange Server logs for relevant threat indicators, ensure a good EDR product to detect behaviors and apply indicators (e.g., Secureworks endpoint agent or one of our endpoint partners), and consider restricting access to the Microsoft Exchange Control Panel (ECP).
- If you are an existing VDR customer: Search for <software“Microsoft Exchange”> for a specific scan and continue to prioritise the highest risk in your environment.





