Google, Microsoft back UK government on cyber security

Major businesses including Google and Microsoft have pledged to help the UK tackle the most damaging cyber security threats. Up to £117 million of private industry investment will be combined with £70 million of government funding through the modern Industrial Strategy to develop new technologies. These will range from a new and secure hardware prototype […]
Register today for the Smarter Payments Summit

You’re about to miss out on the fintech and payment transaction event of the year. The Smarter Payments Summit takes place on September 9th at the Hilton London Tower Bridge, providing a full day of business connections, learning and networking – and it’s free for senior payment transaction and cyber security professionals to attend. Simply register […]
£33m available for quantum security projects

The government has invited businesses to apply for a share of up to £33 million to work with others on developing new products and services that exploit quantum technologies. The second generation of technologies based on new quantum effects promises to deliver more secure digital communication, improved construction and radical increases in computing power. This, […]
FREE GUIDE: How to reduce the security vulnerabilities in Office 365

You’re likely to follow the path of least resistance, attacking wherever you have the biggest chance of success on the most widely used programs. You will put out Phishing emails, Malware attacks, simple extortion mailers and Business Email compromise (BEC) attacks to gain entry to the target system. Many enterprise organisations’ SaaS technology of choice […]
Security IT Summit – Everything you need to know

Are you free on November 5th 2019? Join us at the Security IT Summit– Here’s everything you need to know! The Security IT Summit is a bespoke and highly-targeted one-day event created specifically for senior cyber security professionals like you. It is entirely FREE for you to attend. Simply register your place here. When: 5 November […]
NCSC details key wins in cyber security war

A scam to defraud thousands of UK citizens using a fake email address spoofing a UK airport was one of a wide range of cyber attacks successfully prevented by the National Cyber Security Centre (NCSC) in the last 12 months. Details of the criminal campaign are just one case study of many in Active Cyber Defence […]
UK businesses subjected to one cyber attack every minute in 1Q19
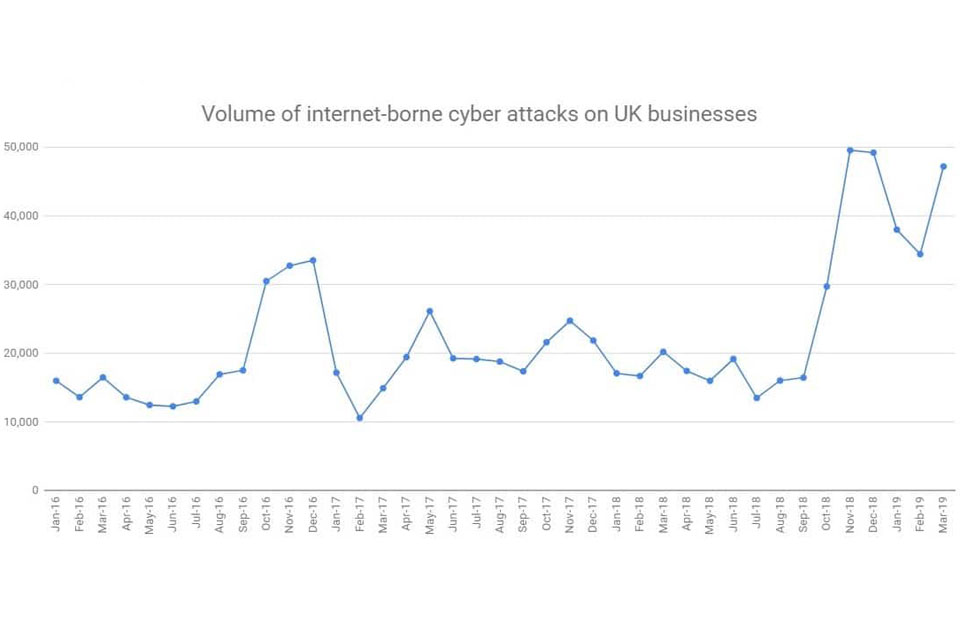
UK businesses were subjected to 119,659 internet-borne cyber attacks each, on average, in the first quarter of 2019, according to analysis by Beaming. This rate of attack, which equates to one every minute, was more than double that experienced in the first three months of 2018, when companies were attacked online 53,981 times on average. […]
Skills shortage and 5G fears at European data centres
Continuing unprecedented demand for new datacentres, fears around the shortage of skilled professionals, concerns about the future disruption of 5G, and the limited impact of Brexit are some of the key findings from the latest industry survey from Business Critical Solutions (BCS). The Summer Report, now in its 10th year, is undertaken by independent research house […]
Security IT Summit – Registration open for new autumn event!

Continued strong demand for places at the Security IT Summit means that we are now hosting this unique one-day event twice a year! And registration is open now for the first autumn Summit. Our Approach Taking place on November 5th at the Hilton London Canary Wharf, the Security IT Summit allows senior cyber security professionals […]
Do you specialise in Penetration Testing? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in August we’re focussing on Penetration Testing solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a Penetration Testing solutions […]
