Global IT spending set to hit $4.7 trillion in 2023, driven by automation

Global IT spending is projected to grow by 4.3% this year to reach $4.7 trillion, with CIOs continuing to lose the competition for IT talent, leading to a shift in spending towards technologies that enable automation and efficiency to drive growth with fewer employees. “Digital business transformations are beginning to morph,” said John-David Lovelock, Distinguished […]
Fintech: How financial technology is benefitting businesses, and impacting security

Is your business operating as efficiently as it could be? For smaller businesses and startups, maximising efficiency can be the difference between surviving and thriving. In today’s rapidly-evolving commercial landscape, being an early adopter of the latest technology can set your business apart from the rest, open the door to a wider market of potential […]
Strengthening Defences: Everything you need to know about penetration testing

In the digital landscape where cyber threats are pervasive, penetration testing stands as a crucial pillar of a robust cybersecurity strategy. Often known as ‘ethical hacking,’ penetration testing involves simulating cyberattacks to identify vulnerabilities within your network, systems, or applications. This primer outlines the key elements of penetration testing for your company… 1. Understanding Penetration […]
You’ll be in good company at the Security IT Summit

The Security IT Summit will provide you with a rare day of industry networking, learning and connection building – join the likes of Addison Lee and Dune today! Built for IT/cyber security professionals, this unique event will enable you to lay the groundwork for your future projects for 2024 and beyond. 9th November 2023 Radisson […]
‘Overwhelmed’ cyber analysts fear their organisation could already be breached

97% of cyber analysts are worried they will miss security events, with 71% admitting their organisation may have been compromised and they don’t know about it yet. That’s according to a study by Vectra AI, which details how analysts are being overwhelmed, as they receive 4,484 alerts on average per day, but can’t cope with […]
Gatekeeping Digital Realms: Top tips for effective Authentication in cybersecurity
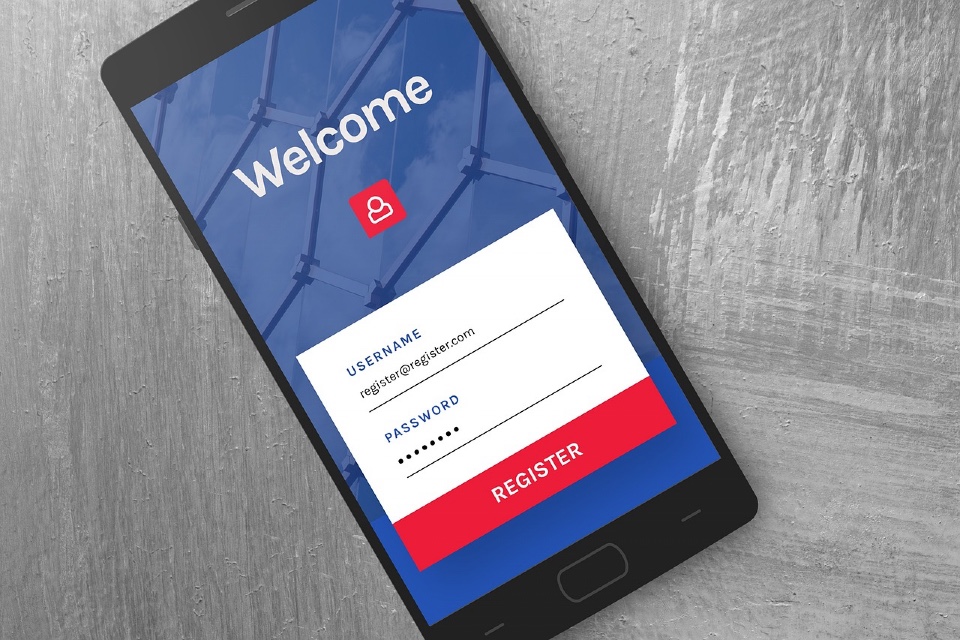
The first line of defence in protecting digital assets and data is effective user authentication. Ensuring the right individuals have access to your systems is paramount to maintaining a robust cybersecurity posture. Here, we explore key tips for optimising your authentication processes… Adopt Multi-Factor Authentication (MFA): MFA adds an extra layer of security to your […]
Amazon drives IaaS market to new highs

The worldwide infrastructure as a service (IaaS) market grew 29.7% in 2022, to total $120.3 billion, up from $92.8 billion in 2021, according to new data. Analysis by Gartner indicates Amazon retained the No. 1 position in the IaaS market in 2022, followed by Microsoft, Alibaba, Google and Huawei. “Cloud has been elevated from a […]
Do you specialise in Penetration Testing? We want to hear from you!
Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in August we’re focussing on Authentication solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re an Authentication solutions […]
The changing role of partners in SAP’s new cloud mindset

Recent changes from SAP has left many partners wondering what the next steps are in providing cloud services, especially given SAP’s insistence on developing a ‘cloud mindset’, and emphasising its Activate Methodology and Fit to Standard workshops to achieve this. Up until this point, a change of direction to the cloud has had little impact […]
Navigating recessionary budget pressures on IT departments

In today’s challenging economic landscape, budgetary pressures have become a reality across every department. None more so than IT. In spite of the promise of increased productivity and performance, advanced technologies such as AI, faster storage, and more secure data inevitably cost more and take longer to deliver than today’s budgets can afford. IT directors […]
