Choosing Secure Web Hosting Environments: Seven top tips for IT Managers

The security of a brand’s website is paramount. For IT managers, selecting a hosting environment is a crucial decision that significantly impacts security, performance, and reliability. So what are the essential factors? Here are seven to get you started… 1. Security Features The foremost consideration is the security features offered by the hosting provider. This […]
MALWARE MONTH: Devising effective anti-malware strategies

In the complex cybersecurity landscape of the UK, Chief Information Security Officers (CISOs) face the daunting task of protecting their organisations against a multitude of evolving malware threats. An effective anti-malware strategy is essential for safeguarding sensitive data and maintaining business continuity. Here we delve into the key considerations that CISOs must weigh when formulating […]
Threat Predictions for 2024: Chained AI and CaaS operations give attackers more ‘easy’ buttons

With the growth of Cybercrime-as-a-Service (CaaS) operations and the advent of generative AI, threat actors have more “easy” buttons at their fingertips to assist with carrying out attacks than ever before. By relying on the growing capabilities in their respective toolboxes, adversaries will increase the sophistication of their activities. They’ll launch more targeted and stealthier […]
Do you specialise in Network Security Management? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in December we’re focussing on Network Security Management solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a […]
Nearly half of EMEA CIOs are shifting to co-owning digital leadership with their CxO peers

Forty-six per cent of CIOs in Europe, the Middle East and Africa (EMEA) are partnering with their CxO peers to bring IT and business area staff together to co-own digital delivery on an enterprise-wide scale. That’s according to Gartner’s annual global survey of CIOs and technology executives, which has found that CIO’s relationship with their […]
MALWARE MONTH: Emerging malware trends and how the UK’s CISOs are having to adapt
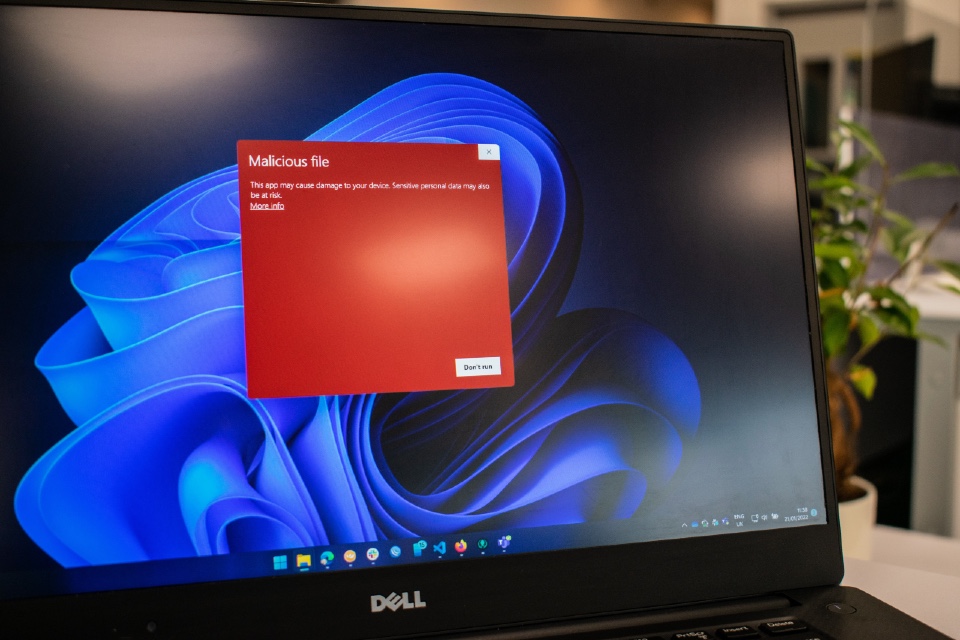
The cybersecurity landscape is being shaped by sophisticated and evolving malware threats on a weekly and even daily basis. Chief Information Security Officers (CISOs) are on the front lines, adapting to these emerging challenges with innovative approaches to protect corporate assets. One of the most concerning trends is the rise of ransomware-as-a-service (RaaS), allowing even […]
SAVE THE DATE: Security IT Summit – June 2024

Couldn’t join us at this week’s Security IT Summit? The next event will take place in London next June – both live and virtual attendance options will be available! 25th June 2023 – Hilton London Canary Wharf – Booking form (flexible attendance options) Benefits of attending include: Receive a bespoke itinerary of relaxed, 1-2-1 meetings with […]
210 million industrial endpoints will be secured by 2028

A new study by Juniper Research has found that there will be growth of 107% over the next five years in the number of industrial endpoints featuring cybersecurity protection. The research identified the rise of interconnected processes within the Industry 4.0 revolution as increasingly exposing critical industrial infrastructure to external threats; requiring wholesale changes in how […]
The Evolution of Employee Cybersecurity Awareness: A tale of of adaptation and education

In the past decade, the digital landscape has grown exponentially, bringing with it a complex web of cybersecurity threats. Amidst this ever-changing terrain, businesses have had to rapidly adapt, realising that technical safeguards alone aren’t sufficient. An informed and vigilant workforce has emerged as the first line of defence against cyber threats. Here we explore […]
Do you specialise in Malware prevention solutions? We want to hear from you!

Each month on IT Security Briefing we’re shining the spotlight on a different part of the cyber security market – and in November we’re focussing on anti-Malware solutions. It’s all part of our ‘Recommended’ editorial feature, designed to help IT security buyers find the best products and services available today. So, if you’re a Malware solutions […]
