Why endpoint security matters more than ever

The swiftly evolving threat landscape, combined with the huge increase in remote working, means that securing your organisation’s endpoints has never been more critical. Here, George Glass, Head of Threat Intelligence at Redscan, explains the importance of endpoint security and why detecting and responding to the latest threats demands greater endpoint visibility and specialist expertise… […]
Identity Access Management vs. Access Rights Management – What’s the Difference?

The terms access management (short: AM; also referred to as access rights management or just rights management) and identity & access management (short: IAM) are often used synonymously. In practice, however, they do not stand for the same thing. In this article, we are going to take a closer look at the difference between access rights management software and identity/access management solutions. Check out the article at https://www.tenfold-security.com/en/identity-access-management-vs-permission-management-whats-the-difference/ If you are […]
Meeting the Tests to get out of Data Lockdown

Digital transformation of any business has always been hampered by making sense of underlying data. And that data has been growing in volume at an unprecedented rate driven by the growth of IoT. It’s the perfect storm – the need for real-time information being increasingly distanced by the rate at which the data volume is […]
User Access Review – What’s That?

By Tenfold Security Users come, they stay, they leave, they move around between departments and they collect privileges on the way. That’s OK, they need privileges to do their jobs. But do they need all the privileges they have, always? That’s a question you need to ask yourself, for every user, repeatedly. This article covers what is meant by a user access […]
Securing a hybrid and agile workforce

2020 has forced businesses to revise many of their operations. One significant transition being the shift to a remote working model, for which many were unprepared in terms of equipment, infrastructure and security. As the Government now urges people to return to work, we’re already seeing a shift towards a hybrid workforce, with many employees splitting their […]
How to block hidden malicious commands in obfuscated scripts

By Chris Corde, VP of Product Management, VMWare Carbon Black For a long time now, our Threat Analysts have flagged the growing threat of script-based attacks, especially from Microsoft PowerShell and Windows Management Interface script commands, and their ability to escape notice in many antivirus solutions. Increasingly, these types of attacks have become the common standard […]
Giving resellers the key to unlocking end user continuity, productivity and flexibility

By Dave Manning, Operations Director, Giacom Until recently, the transition to working from home was unfolding at a gradual pace for many businesses. Although there is much research to back up the benefits of flexible and remote working, many business leaders remained sceptical, believing that office working remained the setup that would be most productive […]
The growing DDoS landscape

By Anthony Webb, EMEA Vice President at A10 Networks Last month, news reports highlighted one of the biggest DDoS attacks ever recorded. The attack, which targeted a large European bank, generated 809m packets per second (Mpps). This is a new industry record for a PPS-focused attack which is more than double the size of previous attacks. A10 Networks recently launched its Q2 2020: State of DDoS Weapons Report, based on […]
Data centre pre-construction – The devil is in the detail

By Jon Healy, Operations Director at Keysource Having a detailed pre-construction phase undertaken before starting the design and build or upgrade of a data centre facility has a number of major benefits, however many organisations choose to sidestep this part of the process. In my experience this is a false economy that can often result in, at […]
In case you missed ZIVVER at the Security IT Summit…
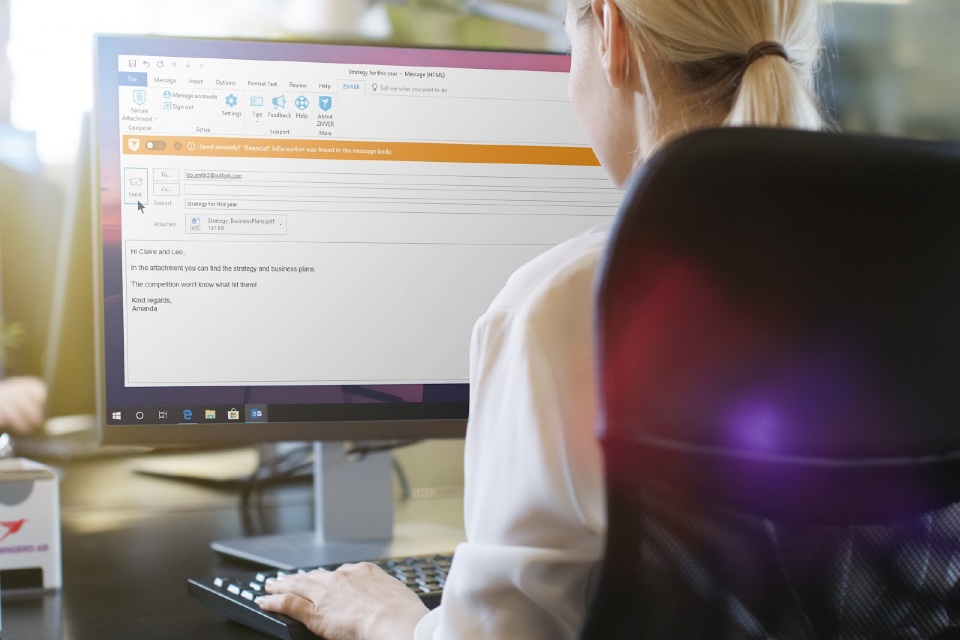
By Zivver Last month marked ZIVVER’s first appearance at the Security IT Summit and we had a great time meeting so many people (virtually). If you took some time during the summit to connect with us, we look forward to staying in touch! And if you missed your chance to meet with us at the […]
